Single sign-on or SSO allows the user to access the THEIA platform using identification from another application. The protocols that can be configured are : Azure AD, JWT, SAML and CAS.
The settings for most of these services (Azure AD, JWT and SAML), subject to user rights, are available in the Management interface in the Parameters > SSO Configuration menu.
The CAS authentication system cannot be set up via the above menu. Please contact our support department for more information.
1. Azure AD
1.1 General configuration
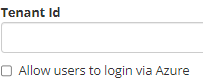
Using the Tenant ID parameter, the platform will be able to identify the Azure AD directory in which user data is stored.
The following boxes authorise users to access the platform via the Azure directory and to automatically create their accounts if they do not already exist. If the account already exists on the platform, its information will be updated each time it is connected, using data from the Azure directory.
1.2. User association
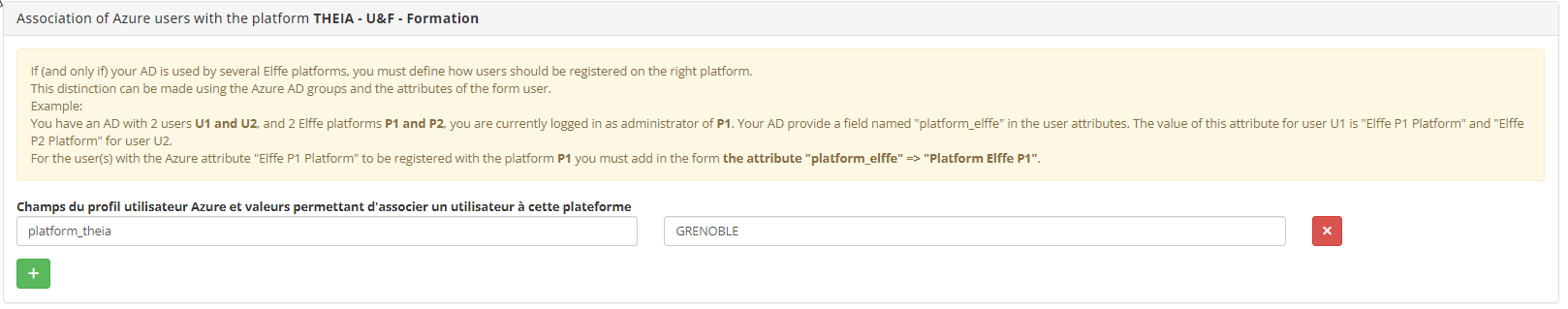
When the Azure directory has users on different platforms, you need to enter the name and the expected value of the attribute. For example, if my directory contains a platform_theia attribute for each of my users with two possible values: GRENOBLE or PARIS, then it is important to indicate this in this space so that the THEIA platform can be correctly identified at each connection.
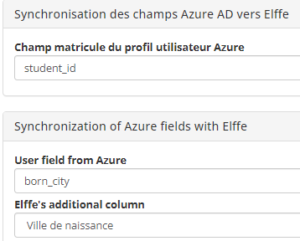
The student number field can also be filled in automatically when the user logs in. The platform retrieves the value of the attribute associated with the configured element (e.g. student_id).
Additional attributes are added, on request, by THEIA in order to enrich user accounts with additional information. These elements can also be taken into account during configuration by first filling in the “Azure user profile field”, then indicating the correspondence at platform level (“Additional ELFFE column).
1.3 Group management
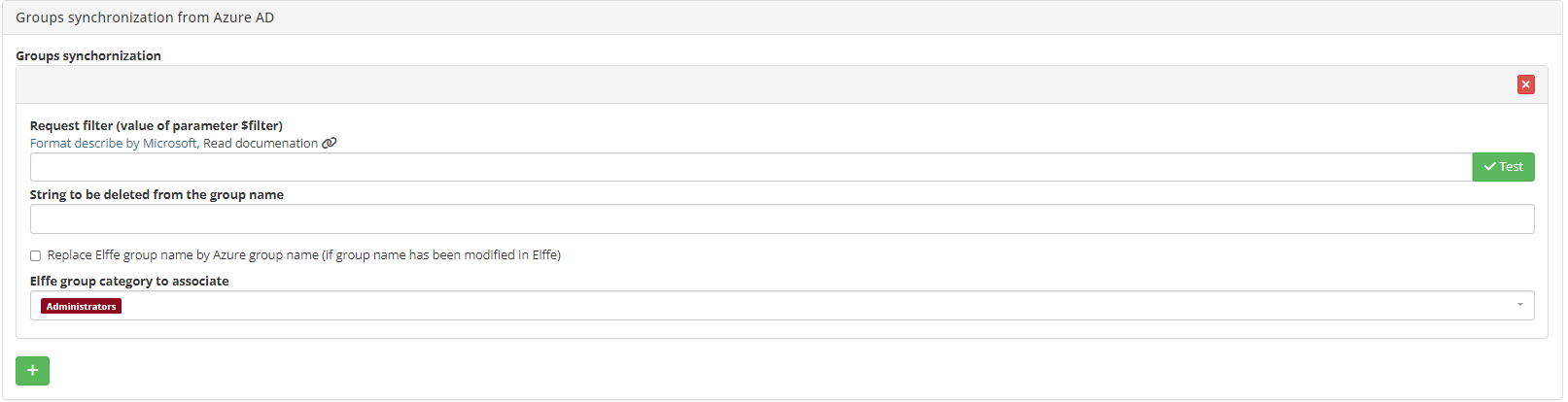
Groups from the Azure directory can be automatically created on the platform thanks to a daily synchronisation task.
Using the first field, you can filter the query to retrieve only the subset of the collection linked to the group. If necessary, unwanted character strings can be removed using the second input field, so that the name of the Azure group matches that of the platform.
The following checkbox authorises the group name on the platform to be modified by the value taken from the Azure directory during daily synchronisation.
When created, the group will be associated with the configured category.
2. JWT
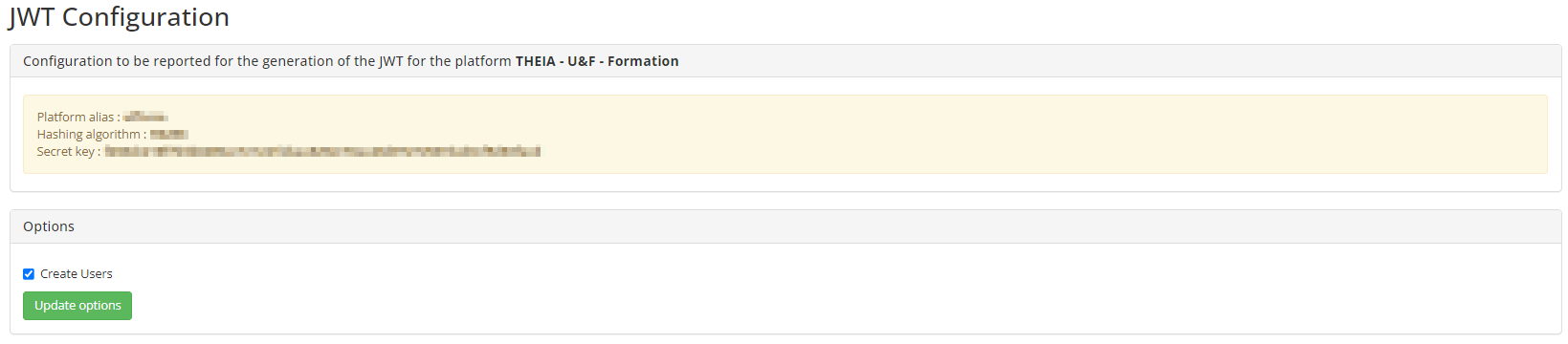
JWT allows users to be identified via an exchange of tokens. This is a .Json format file signed by a long string of characters using the algorithm and the secret key available in the configuration tab. The signature ensures the integrity of the data in the token and guarantees that the data has not been altered since it was created.
The expected information is as follows:
{
“sub”: “string” _Identifier of the user by the client
“preferred_username”: “string” _Identifier of the user by the THEIA platform
“given_name”: “string” _First name
“family_name”: “string” _Last name
“email”: “string” _Email address
“groups”: [“string”, “string”,…] _List of group(s) in which the user is registered
“extraTime”:Boolean _Whether or not the user has been granted extra time
}
The Create users on the fly box allows you to automatically create user accounts on the platform when you first connect. If the account already exists, it will be updated with the information contained in the token.
This means that users can be registered or deregistered from the groups in which they are registered. The user will only be registered in the groups shown in the token. If no group is entered or is not known in the platform, then the user will not be registered in any group.
In addition, the automatic creation of groups is not taken into account by this protocol.
3. SAML
3.1 Identity Provider (IdP)
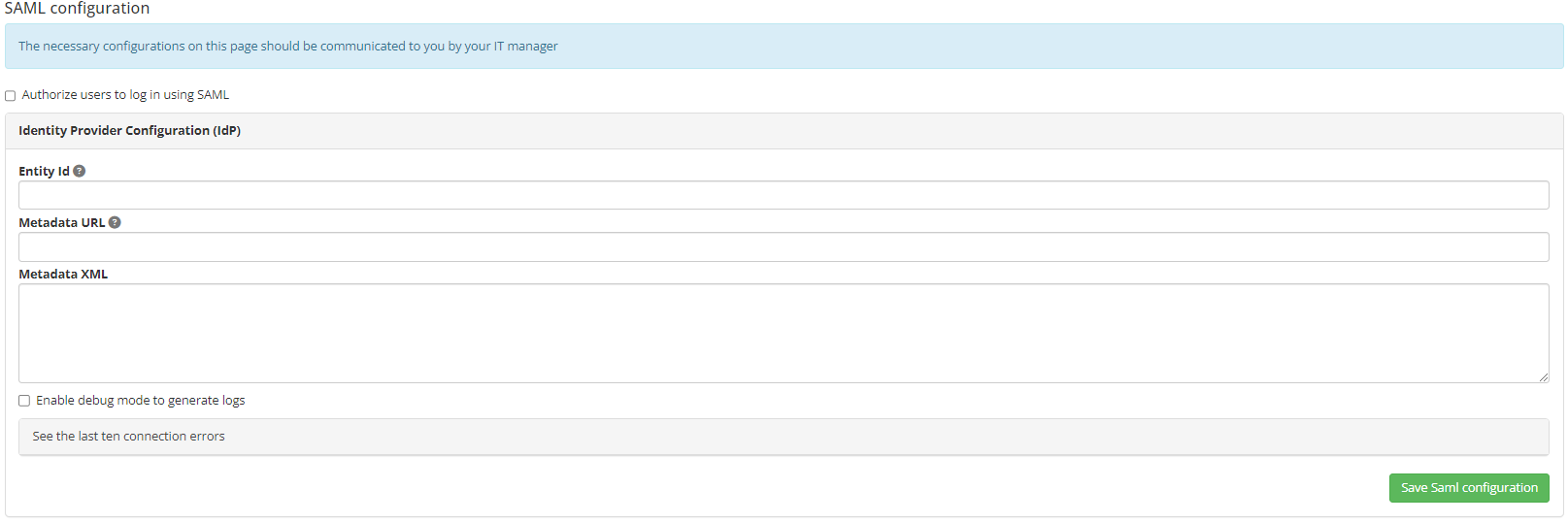
In order to enable communication between the two SAML providers (identity provider and service provider), it is essential to enter either the URL pointing to the .xml metadata file or the content directly in the Metadata XML field.
Note that Entity Id must correspond to the identifier present in the metadata file.
When setting up this service, we recommend activating debug mode to obtain the list of logs. This will make it easier to correct any anomalies.
This configuration enables the transmission of user information and the automatic creation of user accounts on first connection. In addition, using the bulk import function in the Users > User accounts menu, accounts can be created directly on the platform. You will need to ensure that the username attribute supplied at the time of connection matches the THEIA identifier of the account.
3.2 Group management
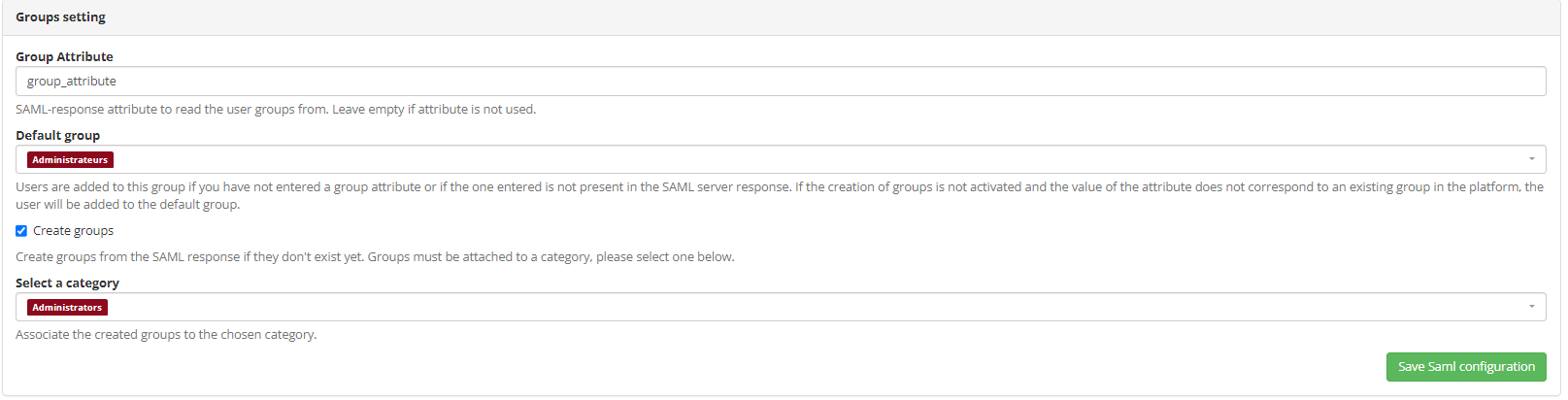
La valeur associée à l’attribut de groupe permet, lors de chaque connexion, d’inscrire l’utilisateur dans l’entité correspondante. Si le groupe n’est pas présent sur la plateforme ou si la valeur de l’attribut est vide, alors l’inscription sera effectuée dans le groupe par défaut. On note qu’un utilisateur ne peut être désinscrit d’un groupe via cette méthode.
En revanche, il est possible de créer ce groupe si celui ci n’existe pas via la case à cocher Créer les groupes. Il dépendra alors de la catégorie renseignée dans le champ Sélectionner une catégorie.
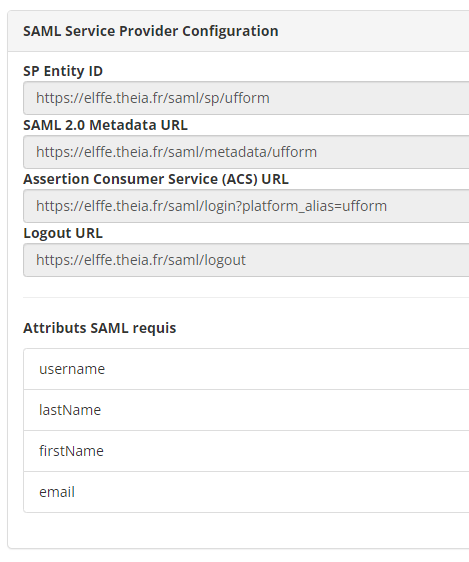
3.3. SAML Service Provider Configuration
The display of this information is conditional on the checkbox Authorise users to connect using SAML. It tells you :
- The service provider’s Entity Id parameter
- The URL to the metadata .xml file, in order to obtain the elements linked to communication between the providers, as well as the expected content
- The ACS URL, which allows the customer to set the access link to the THEIA platform
- The Logout URL, which gives the customer the freedom to configure a possible disconnection from their portal.
As shown in the metadata file, the platform expects a signed assertion. It is important to specify that it also expects the entire response to be signed.